How Quantum Origin works¶
Quantum Origin leverages the inherent unpredictability of quantum behavior to transform unproven or biased local entropy into provably secure randomness, delivered through a software binary in combination with a pre-generated output from Quantinuum’s quantum computer.
This solution operates in two distinct phases. The first is run in advance by Quantinuum using our Quantinuum Systems quantum computers to generate a quantum seed—a set of randomness with mathematically proven entropy. In the second phase, the Quantum Origin software refines local entropy using this seed, producing a continual stream of cryptographically strong, uniform randomness at the endpoint.
Together, these stages provide a scalable, hardware-independent solution for upgrading cryptographic randomness across a wide range of systems—from embedded devices and operating system kernels to HSMs and air-gapped environments.
Phase 1: Quantum Generation – Verifying Quantum Entropy¶
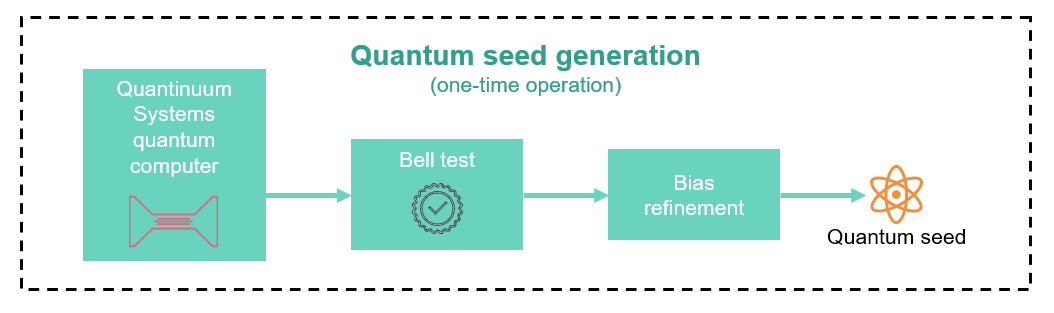
Phase #1: Generation of the quantum seed¶
The process begins with Quantinuum Systems quantum computer, which leverages the fundamental unpredictability of quantum mechanics. When qubits are initialized, placed into superposition, and measured, they collapse into a unpredictable output—yielding either 0 or 1. In an ideal system, this distribution would be perfectly uniform. However, in practice, hardware imperfections and classical measurement processes can introduce bias.
To detect and account for such bias, Quantum Origin performs a Bell test—specifically, a Mermin game, which is a method for confirming that the randomness could not come from comes from a classical or predictable process. This approach, recognized by the 2022 Nobel Prize in Physics, allows us to mathematically confirm that the observed randomness could only have come from genuine quantum processes.
In the Mermin game, the system repeatedly prepares and measures three entangled qubits. If the results show patterns that can’t be explained by any classical system, or ‘wins’ the game with high probability, the test confirms that the randomness is genuinely quantum in origin. From this, we calculate a guaranteed minimum level of unpredictability, or the lower bound on min-entropy. The percentage of rounds that “win” the game,referred to as the violation of the Bell inequality, directly determines this bound.
Following this verification, the raw quantum output is passed through a two-source randomness extractor. This cryptographic post-processing step removes residual bias and refines the output into a uniform distribution. The result is the quantum seed: a high-entropy binary string with a proven min-entropy rate of 1.0, meaning every bit is statistically indistinguishable from ideal randomness.
Note
The quantum seed is mathematically proven to be indistinguishable from perfect entropy, with a protocol error below 2⁻¹²⁸. It serves as the foundation for all subsequent entropy amplification in the local environment.
Phase 2: Software Deployment – Local Entropy Amplification¶
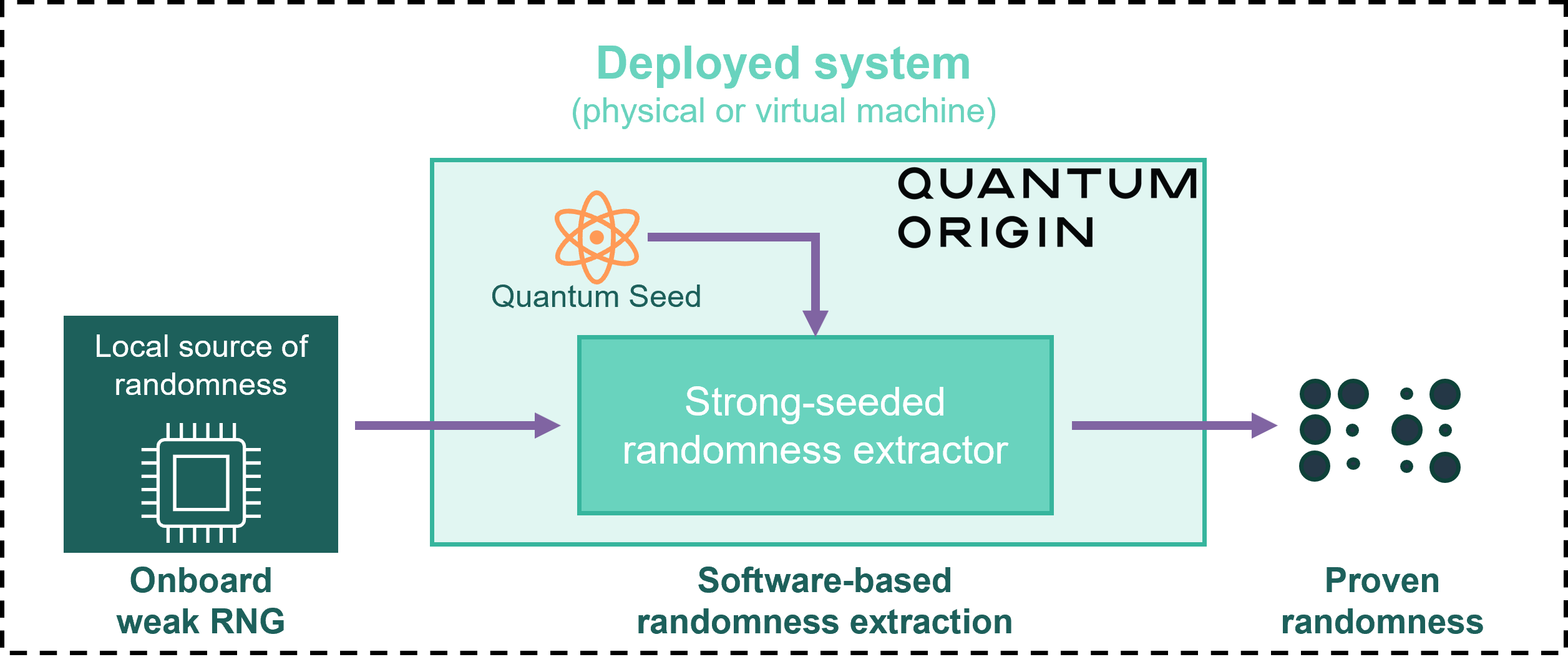
Phase #2: Local generation of proven randomness¶
Once generated, the quantum seed is packaged alongside the Quantum Origin software binary, which is deployed to local systems—entirely offline and without dependencies on quantum hardware.
When executed, Quantum Origin reads from a local source of unproven private entropy, such as CPU-generated values (e.g., RDSEED), CPU jitter, or other available onboard randomness sources. It then uses a strong-seeded extractor, an information-theoretically secure algorithm to refine a private weak and biased source into high-quality entropy using the quantum seed. This produces the final output, which is:
Uniform: Each bit has an equal probability of 0 or 1
Independent: No correlations between output values
Proven: Output entropy strength is based on mathematical proofs
Because the quantum seed proven and does not need to be secret, and the local source is private, the extractor guarantees that the final output is cryptographically secure—even if an attacker knows the seed and the extractor algorithm in full.
Seamless deployment and integration on endpoints¶
Quantum Origin’s architecture is designed for secure integration into modern and legacy systems alike:
Hardware-agnostic: Runs on standard CPUs (Intel, AMD, ARM, RISC-V) without additional hardware
Air-gapped ready: Fully operational in disconnected and offline environments
Flexible deployment: Available as a CLI, SDK, OS reseed adapter (Windows CNG, Linux entropy pool), or HSM connector
Compliance-ready: Conforms to NIST SP 800-90B (Cert #E214) and supports deployment in FIPS 140-3 environments
By embedding provable quantum entropy directly into your existing infrastructure, Quantum Origin enables a foundational upgrade to cryptographic strength—without disruption. It delivers a measurable, repeatable process for producing high-quality entropy—grounded in quantum physics, validated with peer-review scientific process, and delivered through software.
More information on our process can be found in the technical white paper.